PHPMyAdmin Bypass via Publicly Accessible .env File
Overview
During a recent security assessment, I uncovered a critical vulnerability in a web application that allowed unauthorized access to the entire database via a publicly accessible .env file. This led to the successful bypass of PHPMyAdmin authentication and direct access to sensitive data.
This blog walks through the steps taken during the discovery, highlights the risk, and provides mitigation strategies to prevent such exposures in production environments.
🔍 What Is a .env File?
A .env file is typically used in web applications (especially those built with frameworks like Laravel or Node.js) to store environment variables, including sensitive configuration data like:
- Database credentials
- Mail server settings
- API keys
These files are meant to be private and server-side only, never exposed to the web.
🚨 The Vulnerability: Unrestricted Access to .env File
While browsing through the site structure and performing common wordlist enumeration, I found that navigating to the /cpanel/.env endpoint revealed the .env file in plain text. No authentication or access control was in place.
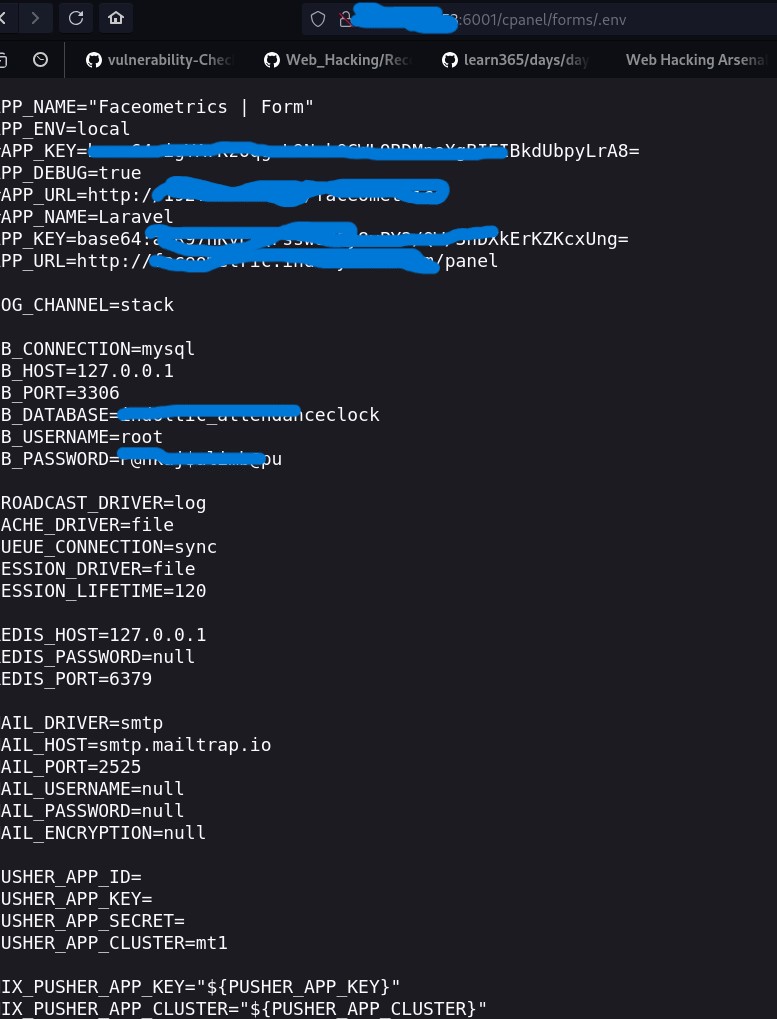
Sample of exposed data (sanitized):
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=[REDACTED]
DB_USERNAME=[REDACTED]
DB_PASSWORD=[REDACTED]
💥 Exploiting the Misconfiguration
Once I had the credentials, I attempted to access the PHPMyAdmin interface, which was also publicly exposed.
Steps Taken:
- Accessed the
.envfile:http://[REDACTED_IP]:[PORT]/cpanel/.env - Extracted the credentials from the response.
- Navigated to the PHPMyAdmin panel:
http://[REDACTED_IP]:[PORT]/phpmyadmin - Entered the exposed database username and password.
- Logged in successfully.
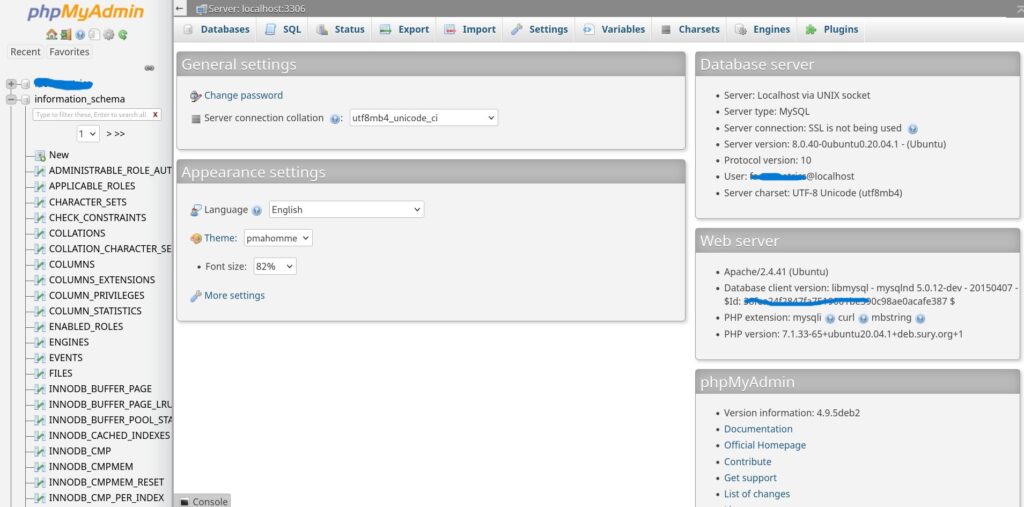
This granted full access to the database, including potentially sensitive user data, logs, and administrative information.
🧨 Impact
The implications of this vulnerability are severe:
- Data Theft: Unauthorized access to personal or financial data.
- Data Tampering: Attacker can alter or delete records.
- Pivoting: Use the database access to explore further lateral movement.
- Reputation Loss: Public exposure can damage user trust and brand image.
- Compliance Violation: Especially critical if the app stores data under GDPR, HIPAA, etc.
✅ Recommended Mitigation
1. Restrict Access to .env Files
Never expose configuration files over the web. For Apache:
apacheCopyEdit<Files ".env">
Require all denied
</Files>
For Nginx:
nginxCopyEditlocation ~ /\.env {
deny all;
}
2. Harden PHPMyAdmin Access
- Limit access via IP whitelisting.
- Place PHPMyAdmin behind HTTP authentication.
- Disable it entirely in production environments, if possible.
3. Rotate & Secure Credentials
- Immediately change exposed credentials.
- Store sensitive configuration outside web root.
- Use environment variables securely within your deployment pipeline (Docker, CI/CD, etc).
4. Automate Checks
Use tools like:
Nikto,dirsearch,gobusterfor file discovery.- Web Application Firewalls (WAF) to filter suspicious access patterns.
- CI/CD pipeline scanners to prevent committing secrets in repos.
📌 Final Thoughts
This case highlights the real-world danger of small oversights — like a forgotten .env file — leading to massive breaches. Web developers and DevOps teams must work hand-in-hand to harden deployments, apply the principle of least privilege, and ensure no sensitive endpoints are left publicly accessible.
Remember, security is not a feature — it’s a mindset.

